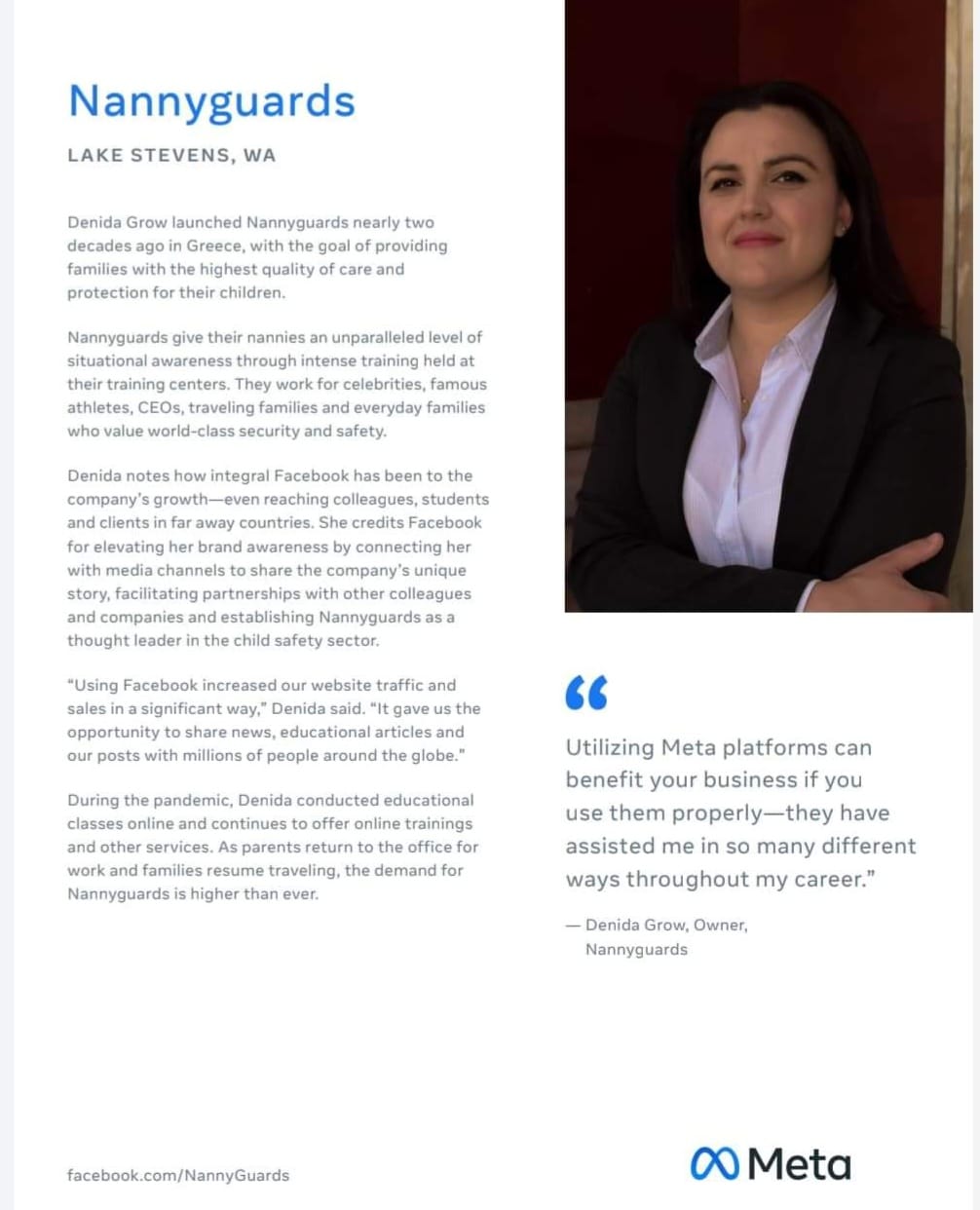
Category: Nannyguards
-
Do you want to know how to keep your children safe? Start with these simple steps
Parents! You REALLY need to start paying attention: Children and teenagers should be taught that their safety should be a top priority for them. As they navigate the world, and whether they are at home, school, or out with friends, it’s important to be aware of potential dangers and to take steps to stay safe.…
-
‘Wren Eleanor’ TikTok movement inspires moms on social media to remove photos of kids: ‘Sick people’
TikTok sleuths noticed that users were saving videos of 3-year-old Wren Eleanor in concerning numbers For years, security professionals have been repeatedly sounding the alarm in regards to the extreme danger of parents posting their children’s pictures or videos online. Your child’s adoring pictures or videos can be downloaded, used, and, quite often, photoshopped in…
-

Confidentiality: Personal Choice or Professional code of conduct?
Recently, a young lady, new to the industry, raised a question on a social platform questioning the practice of, or if it is acceptable for, people in our industry to be dropping clients’ names in public or publicly posting pictures with their clients. Surprisingly, many people who took part in the thread commented saying that…
· Athena Bodyguards, ATHENA Worldwide Categories, Bodyguard Careers, Bodyguard Lessons, Bodyguard Training, Bodyguards in USA, British Female Bodyguards, Celebrity Bodyguards, Child Protection, Child Protection Specialist, Close Protection Training, Dignitary Protection, Diplomatic Protection, Executive Protection Training, female bodyguard careers, female bodyguards, female close protection, female executive protection, Female self defense, Mannyguards, Nanny Training, Nannyguard, Nannyguards, Protective Intelligence, UK bodyguards -
Executive Protection – Realities of the Industry and the Ugly Truth
Let’s talk about the real world of Executive Protection with all its fantasy myths and all its brutal truths. Many newcomers in our Craft have a completely different idea of what the profession truly is or what it appears to be, because their view is primarily based on what they have heard, seen in staged…
· Athena Bodyguards, ATHENA Worldwide Categories, Bodyguard Careers, Bodyguard Lessons, Bodyguard Training, Bodyguards in USA, British Female Bodyguards, Celebrity Bodyguards, Child Protection, Child Protection Specialist, Close Protection Training, Counterterrorism, Dignitary Protection, Diplomatic Protection, Event Security, Executive Protection Training, female bodyguard careers, female bodyguards, female close protection, female executive protection, Female self defense, Mannyguards, Nanny Training, Nannyguard, Nannyguards, Protective Intelligence, secret service, UK bodyguards