Category: Asset Protection
-

Identifying Suspicious Behavior: Essential Pre-Attack Indicator Training for Executive Protection Agents
An article by Bob Duggan, Founder & President, Executive Security International Senior executive protection professionals will all agree that the number one goal when performing protective details is to prevent a threatening or embarrassing situation before it becomes a reality for your client. Now, we all know that the majority of EP schools are highly…
-
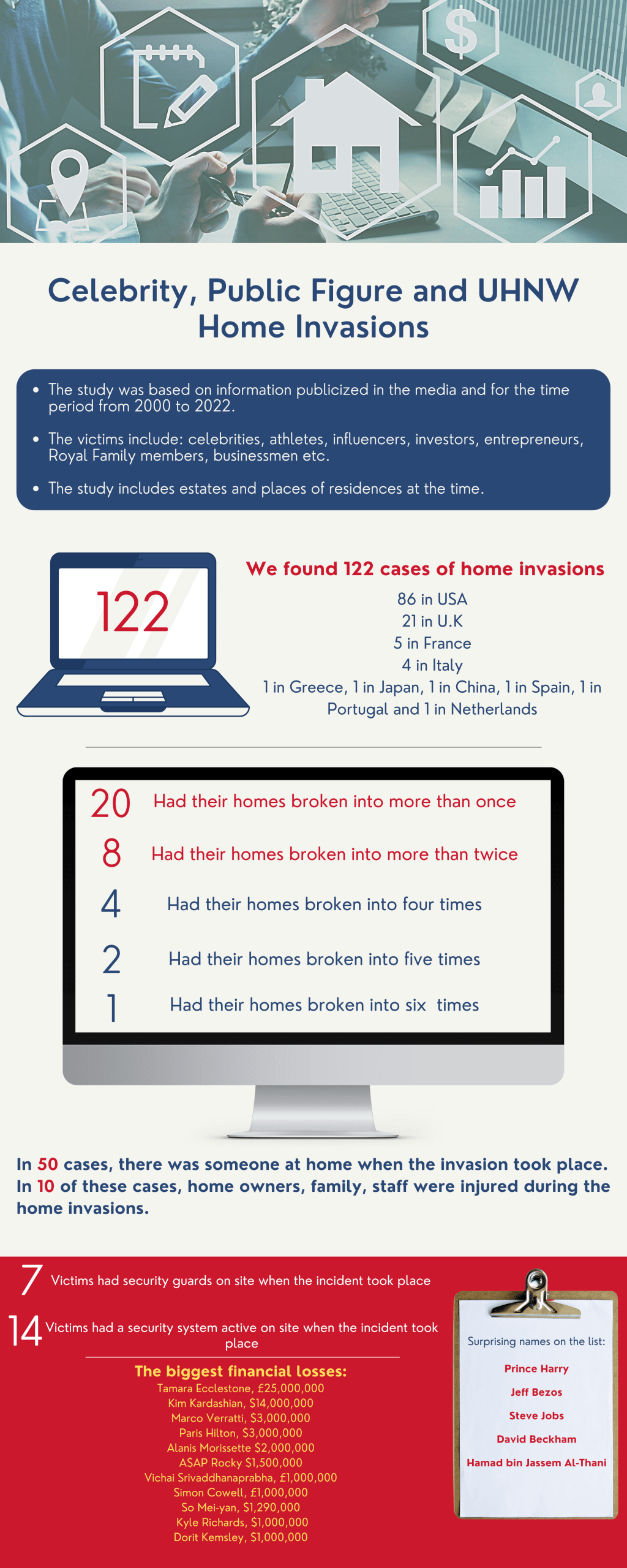
Residential Security-It is more important than you think
What do celebrities like Piers Morgan, Tyler Perry, Paris Hilton, Simon Cowell, Ariana Grande, Kate Moss, Kim Kardashian, Rita Ora, Rihanna, Hilary Duff, Lindsay Lohan, Dorit Kemsley, Bella Thorn, Kelly McGillis, Chris Brown, Miley Cyrus, Kanye West… (Yeah, the list is a bit long, isn’t it? Wait though, we’re not done yet…), Sandra Bullock, Selena…
-
Russian Oligarchs Keep Getting In Troubles by Instagram Selfies
In our latest interview with expert Nick Barreiro, Chief Forensic Analyst of Principle Forensics, we discussed the security risks from any/all social media platform postings and how someone can obtain critical information from your pictures. If you haven’t watched the interview yet, please find it below According to Vice’s latest article, authorities have been following…
· Asset Investigation, Asset Protection, Asset Recovery, Athena Bodyguards, Bodyguard Careers, Bodyguard Lessons, Bodyguard Training, Bodyguards in USA, British Female Bodyguards, Celebrity Bodyguards, Child Protection, Child Protection Specialist, Close Protection Training, Conflict Management, Contract Management, Corporate Security, Counter Surveillance, Counter-Terrorism, Counterterrorism, Dignitary Protection, Diplomatic Protection, Domestic Terrorism, Executive Protection, Executive Protection Companies, Executive Protection Training, female bodyguard careers, Female Bodyguards, female close protection operatives, female executive protection, hire a bodyguard, intelligence, intelligence analysis, intelligence analyst, intelligence report, intelligence reports, investigations, Kidnapped, marketing for security, marketing tips for bodyguards, osint, paparazzi, Protective Intelligence, Risk Assessment, risk management, risk mitigation, security companies, security family offices, Security for Royal Family, security manager, security vetting, social media investigations, social media monitoring, SOCMINT, surveillance, threat assessment, travel security, UK bodyguards, vulnerability assessment -

Social Media Investigations and Monitoring for Risk Mitigation Purposes
The use of social media and the way it affects our lives and businesses have brought a new challenge to the security industry and the protective team’s responsibility. It gives the entire world the ability to look into people’s lives with the mere push of a button. Scandals are created, secrets exposed, and lives ruined.…
· Aggression Management, Asset Investigation, Asset Protection, Asset Recovery, Athena Bodyguards, ATHENA Worldwide Categories, Bodyguard Careers, Bodyguard Lessons, Bodyguard Training, Bodyguards in USA, British Female Bodyguards, Celebrity Bodyguards, Child Protection, Child Protection Specialist, Close Protection Training, Conflict Management, Contract Management, Corporate Security, Counter Surveillance, Counter-Terrorism, Counterterrorism, Dignitary Protection, Diplomatic Protection, Domestic Terrorism, Event Security, Executive Protection, Executive Protection Companies, Executive Protection Training, female bodyguard careers, Female Bodyguards, female close protection operatives, female executive protection, Female self defense, hire a bodyguard, HUMINT, intelligence, intelligence analysis, intelligence analyst, intelligence report, intelligence reports, investigations, Kidnapped, Mannyguards, marketing for security, marketing tips for bodyguards, Nannyguard, Nannyguards, osint, paparazzi, Protective Intelligence, Risk Assessment, risk management, risk mitigation, RTVAs, secret service, security companies, security family offices, Security for Royal Family, security manager, security vetting, social media investigations, social media monitoring, SOCMINT, surveillance, terrorist, threat assessment, travel logistics, travel security, UK bodyguards, vulnerability assessment, workplace violence, workplace violence prevention -
Mentoring Security Professionals
Mentoring Security Professionals. LeMareschal and Athena Worldwide will be launching a series of educational webinars that are absolutely free to attend. The aim of the webinars won’t be to present people and their past stories, but to have specific guests who will combine their experience and training in the industry in order to teach you…
· Aggression Management, Asset Investigation, Asset Protection, Asset Recovery, Athena Bodyguards, ATHENA Worldwide Categories, Bodyguard Careers, Bodyguard Lessons, Bodyguard Training, Bodyguards in USA, Celebrity Bodyguards, Child Protection, Child Protection Specialist, Close Protection Training, Conflict Management, Contract Management, Corporate Security, Counter Surveillance, Counter-Terrorism, Counterterrorism, Diplomatic Protection, Domestic Terrorism, Event Security, Executive Protection, Executive Protection Companies, Executive Protection Training, female bodyguard careers, Female Bodyguards, female close protection operatives, female executive protection, hire a bodyguard, HUMINT, intelligence analysis, intelligence reports, investigations, Kidnapped, Mannyguards, Nannyguard, Nannyguards, osint, paparazzi, Protective Intelligence, risk management, risk mitigation, RTVAs, secret service, security companies, security family offices, Security for Royal Family, security manager, security vetting, social media investigations, social media monitoring, SOCMINT, surveillance, terrorist, threat assessment, travel logistics, travel security, UK bodyguards, vulnerability assessment, workplace violence, workplace violence prevention -
Executive Protection Agents in a Rare Interview with a Retired Paparazzi
It’s not very often when we have the ability to interview and learn from our adversaries. While most efforts are seemingly focused only on physical attacks, they do not give enough emphasis to the paparazzi, media, and all that this facet of protection entails. But we’ve got you covered. This is an interview we have…
· Aggression Management, Asset Investigation, Asset Protection, Asset Recovery, Athena Bodyguards, ATHENA Worldwide Categories, Baby Archie Security, Bodyguard Careers, Bodyguard Lessons, Bodyguard Training, Bodyguards in USA, British Female Bodyguards, Celebrity Bodyguards, Child Protection, Child Protection Specialist, Close Protection Training, Conflict Management, Contract Management, Corporate Security, Counter Surveillance, Counter-Terrorism, Counterterrorism, Dignitary Protection, Diplomatic Protection, Domestic Terrorism, Event Security, Executive Protection, Executive Protection Companies, Executive Protection Training, female bodyguard careers, Female Bodyguards, female close protection operatives, female executive protection, hire a bodyguard, HUMINT, intelligence analysis, intelligence reports, investigations, Nannyguard, Nannyguards, osint, paparazzi, Protective Intelligence, Risk Assessment, risk management, risk mitigation, security companies, security family offices, Security for Royal Family, security manager, security vetting, social media investigations, social media monitoring, SOCMINT, surveillance, threat assessment, travel logistics, travel security, UK bodyguards, vulnerability assessment, workplace violence, workplace violence prevention -
The challenges for protecting Public Figures- The Macron Incident
The challenges for protecting Public Figures- The Macron Incident. The latest incident with French President Emmanuel Macron being slapped by someone in the crowd has once again fired up the keyboard warriors who take any incident (video or picture) such as this and claim how improperly the Executive Protection team functioned and what would they have done…
· Aggression Management, Asset Investigation, Asset Protection, Asset Recovery, Athena Bodyguards, ATHENA Worldwide Categories, Bodyguard Careers, Bodyguard Lessons, Bodyguard Training, Bodyguards in USA, British Female Bodyguards, Celebrity Bodyguards, Child Protection, Child Protection Specialist, Close Protection Training, Conflict Management, Contract Management, Corporate Security, Counter Surveillance, Counter-Terrorism, Counterterrorism, Dignitary Protection, Diplomatic Protection, Domestic Terrorism, Emmanuel Macron, Event Security, Executive Protection, Executive Protection Companies, Executive Protection Training, female bodyguard careers, Female Bodyguards, female close protection operatives, female executive protection, hire a bodyguard, HUMINT, intelligence analysis, intelligence reports, investigations, Nannyguard, Nannyguards, osint, paparazzi, Protective Intelligence, Risk Assessment, risk management, risk mitigation, RTVAs, secret service, security companies, security family offices, Security for Royal Family, security manager, security vetting, social media investigations, social media monitoring, SOCMINT, surveillance, terrorist, threat assessment, travel logistics, travel security, UK bodyguards, vulnerability assessment, workplace violence, workplace violence prevention -
Things to consider before you hire an Executive Protection team aka Bodyguards
Things to consider before you hire an Executive Protection team aka Bodyguards. At some point in your careers, you will most likely find the need to retain, or at the very least, inquire about close protection services for yourselves, your loved ones and possibly for those you employ closest to you. Now,…
· Aggression Management, Asset Investigation, Asset Protection, Asset Recovery, Athena Bodyguards, ATHENA Worldwide Categories, Bodyguard Careers, Bodyguard Lessons, Bodyguard Training, Bodyguards in USA, British Female Bodyguards, Celebrity Bodyguards, Child Protection, Child Protection Specialist, Close Protection Training, Conflict Management, Contract Management, Corporate Security, Counter Surveillance, Counter-Terrorism, Counterterrorism, Dignitary Protection, Diplomatic Protection, Domestic Terrorism, Event Security, Executive Protection, Executive Protection Companies, Executive Protection Training, female bodyguard careers, female close protection operatives, female executive protection, hire a bodyguard, HUMINT, intelligence analysis, intelligence reports, investigations, Kidnapped, Nannyguard, Nannyguards, osint, paparazzi, Protective Intelligence, Risk Assessment, risk management, risk mitigation, RTVAs, secret service, security companies, security family offices, Security for Royal Family, security manager, security vetting, social media investigations, social media monitoring, SOCMINT, surveillance, terrorist, threat assessment, travel logistics, travel security, UK bodyguards, vulnerability assessment, workplace violence, workplace violence prevention -
The importance of being a responsible and safety-conscious citizen in your community
Leaving the comfort of your couch and going out to see what’s taking place can save people’s lives. Criminals don’t want to be captured and usually flee if confronted by witnesses. Making criminals aware that someone is watching is a powerful deterrent to their criminal activity and makes for a much safer community
· Aggression Management, Asset Investigation, Asset Protection, Asset Recovery, ATHENA Worldwide Categories, Bodyguard Careers, Bodyguard Lessons, Bodyguard Training, Bodyguards in USA, British Female Bodyguards, Celebrity Bodyguards, Child Protection, Child Protection Specialist, Close Protection Training, Conflict Management, Contract Management, Corporate Security, Counter Surveillance, Counter-Terrorism, Dignitary Protection, Diplomatic Protection, Domestic Terrorism, Event Security, Executive Protection, Executive Protection Companies, Executive Protection Training, female bodyguard careers, Female Bodyguards, female close protection operatives, female executive protection, Female self defense, hire a bodyguard, HUMINT, intelligence analysis, intelligence reports, investigations, Kidnapped, Mannyguards, marketing for security, marketing tips for bodyguards, Nanny Training, Nannyguard, Nannyguards, osint, paparazzi, Protective Intelligence, risk management, risk mitigation, RTVAs, security companies, security family offices, Security for Royal Family, security manager, security vetting, social media investigations, social media monitoring, SOCMINT, threat assessment, travel logistics, travel security, UK bodyguards, vulnerability assessment, workplace violence, workplace violence prevention
